Contact us: info@tenendo.com
Sometimes, a secured infrastructure can fall to a successful phishing attack or an internal adversary.
Historically, adversary simulations were conducted with employee-level access to the internal on-premise infrastructure. This approach is not adapted to modern development and application deployment processes, causing important access control vulnerabilities to be overlooked, leading to catastrophic effects, as seen in the recent attack on Twitter. During the attack, a successful compromise of a developer account leads to access to the entire authentication mechanism. To combat attacks like these, we have decided to consider a new service — developer/DevOps adversary simulation.
The testing process starts with valid developer credentials for the infrastructure and simulates post-exploitation activities after obtaining access to existing CI/CD, logging, monitoring, and remote access solutions as a generic developer to build a complete threat model, find access control misconfigurations, and help companies ensure no single person can cause a compromise.
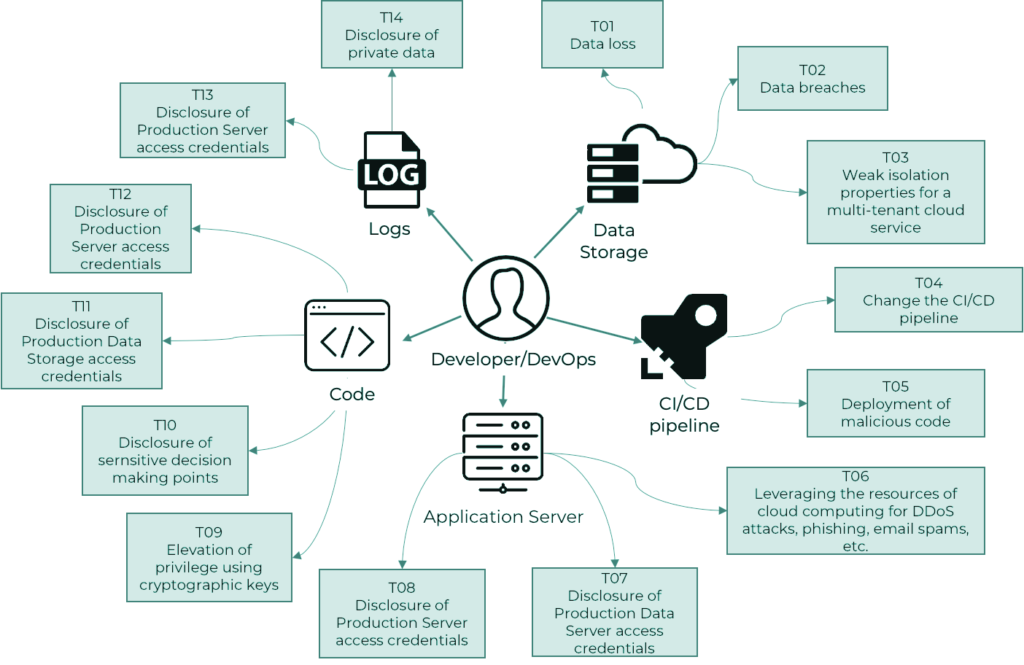
If you think this can be useful to you and your partners or consider using this service to secure your development and deployment processes, please contact us for details and delivery process description.
Other services:
-
Application penetration testing
For all penetration tests, our team collects relevant information about the scope, develops an attack surface, and begins an extensive manual and automated search for vulnerabilities and applicable attacks.
-
Security Code Review
Tenendo code review approach leads to detecting many vulnerabilities in real-world software and achieving amazing results, in comparison to other approaches.
-
Purple Team Services
We run coordinated Red/Blue exercises where our operators attack your infrastructure while working directly with your security team to improve detection and response. No theatrics—just practical testing that identifies real gaps and builds internal capability.
