Contact us: info@tenendo.com
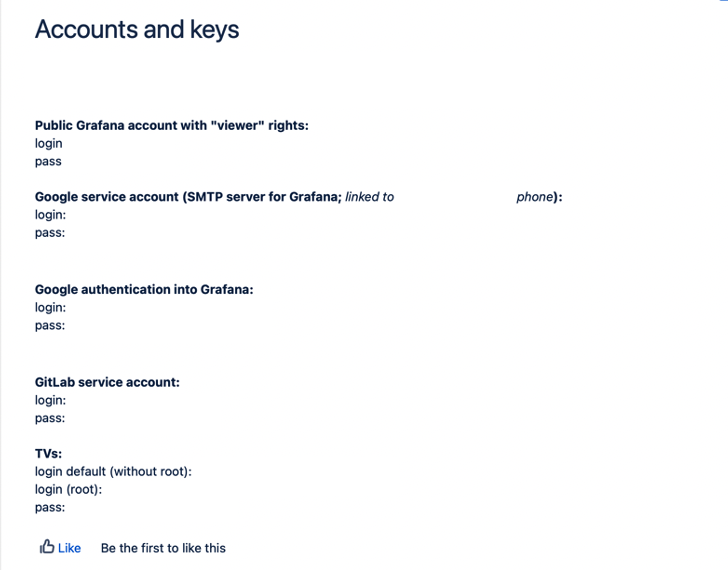
Public info: threat model
Storage buckets, static landing pages and other static content
- can be enumerated, sometimes surprisingly so
- ranges from
.gitand deploy scripts to secrets in static JS - can contain secrets that are only usable in the application context (e.g. session encryption keys)
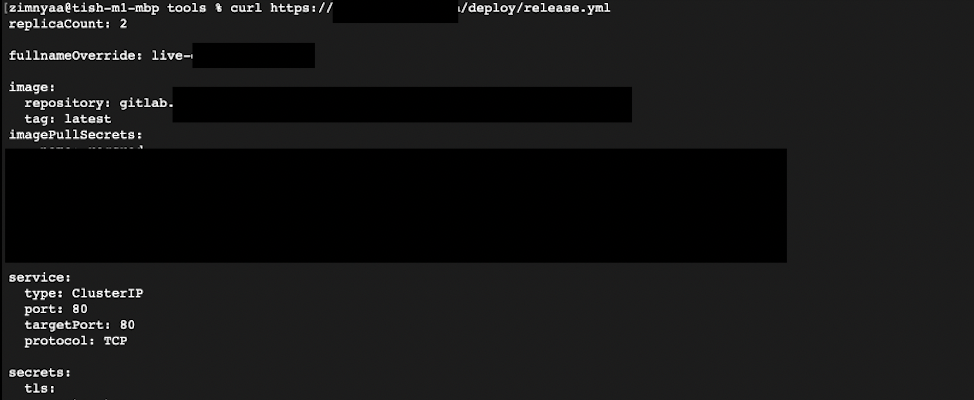
Landings and static content: example
A landing page deployed automatically may contain this:
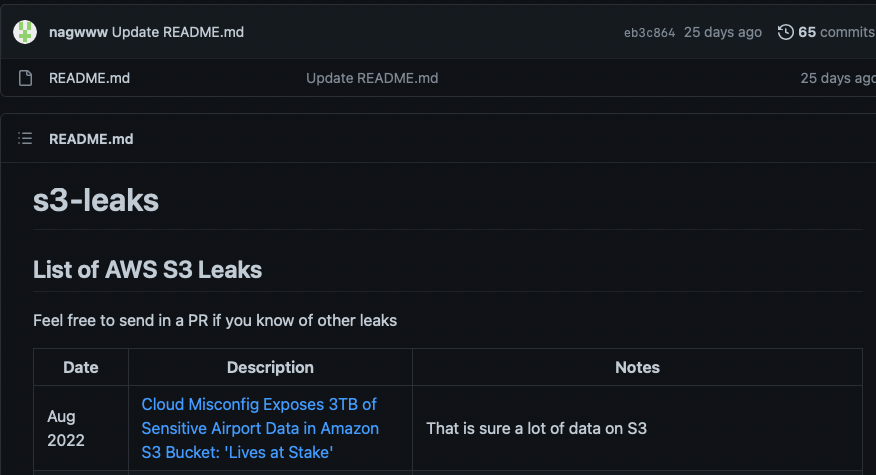
Buckets: examples
lots of “lists of shame”:
Third-party services
A list of examples ordered by frequency of exploitation:
- File sharing solutions (the worst of them all)
- Jira/Confluence/other knowledge bases
- Backup solutions especially self-developed ones
Third-party services: what can happen
This: